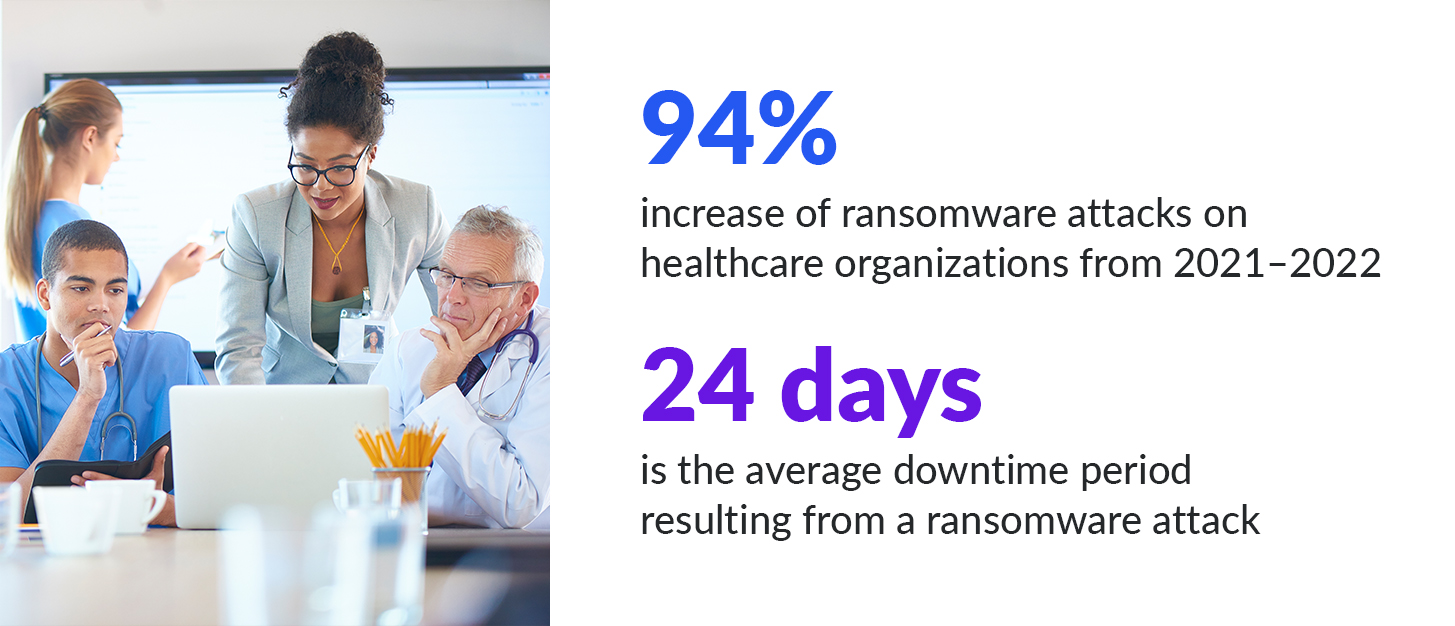
Ransomware attacks pose a serious risk to hospitals nationwide and the latest data suggests the problem is getting worse by the day. According to cybersecurity firm Sophos, the number of ransomware attacks on healthcare organizations increased 94% from 2021 to 2022, exposing nearly 52 million patient records.
The federal government corroborated this concern in a warning statement issued by the FBI, the Treasury Department and the Cybersecurity and Infrastructure Security Agency (CISA). The agencies noted that North Korean hackers have been using a strain of ransomware called “Maui” to attack U.S. hospitals since mid-2021. It’s believed that these hackers are raising money for the North Korean government by charging ransom payments to unlock the health systems’ critical IT systems.
Regardless of the perpetrator or their motive, healthcare organizations everywhere are working to minimize their vulnerability to hackers. They have come to the conclusion that it is only a matter of when, not if, they are targeted by cybercriminals. Furthermore, Hurricane Ian offered a reminder that not all unplanned downtime events are the result of criminal activity.

The outcome is the same whether the event is man-made or natural. Whenever critical healthcare information systems are compromised, patient safety is jeopardized, the quality of care suffers and organizational efficiency plummets. The question is, what can be done about it?
This blog will examine five approaches to mitigating the risk of unplanned downtime in a healthcare environment.
#1: Planning for the worst case
The Joint Commission recently proposed a number of ways that healthcare organizations can protect themselves from the adverse effects of cyberattacks. Several of their recommendations can be summed up by the concept of planning for the worst-case scenario.
- Organizations should conduct detailed “hazards vulnerability analyses” and then plan for life- and safety-critical technology being offline for a month or more.
- Multidisciplinary planning committees representing every significant stakeholder group in the organization should be created to outline specific preparedness actions and mitigation steps.
- Interdisciplinary response teams should be designated to assess the severity of an attack as it happens, determine whether full “downtime mode” is warranted, and direct staff to act accordingly to ensure patient safety.
- All of these strategies, in turn, should be reviewed and updated regularly to ensure a continuous state of readiness.
#2: Stockpiling pre-printed clinical forms
An immediate concern whenever a hospital’s IT network is interrupted is the loss of access to clinical forms. Without them, something as simple as prescribing a medication or discharging a patient requires an error-prone workaround. These risks are compounded when medical procedures requiring informed consent are involved.
A common approach to this risk is to pre-print vital clinical forms –including those that otherwise exist only in digital form –and place them in storage to await an unplanned downtime event. While certainly better than nothing, it's worth noting that this strategy is fraught with problems.
- Clinical forms are constantly changing. Pre-printing and placing clinical forms in storage essentially guarantees that outdated forms will be used in the event of a downtime emergency.
- Stockpiling pre-printed documents, especially those prone to frequent obsolescence, is enormously wasteful. A hospital system will likely need to discard entire pallets full of paper documents as the pre-printed forms become too outdated to use.
- Converting a digital form to a stockpiled paper equivalent contradicts the intent behind the Meaningful Use of electronic health records (EHRs). While it may be necessary to use a paper facsimile of a form during a downtime crisis, it would be best to start with the most current (i.e., digital) version of that form.
#3: Employee training
Employee training can substantially reduce a healthcare system’s vulnerability to ransomware and malware attacks. The cybersecurity awareness experts at KnowBe4 released a Phishing by Industry Benchmarking Report as a way of measuring an organization’s risk of succumbing to a phishing or social engineering scam.
A Wall Street Journal article provides another example. Children’s National Hospital in Washington, D.C., has trained its employees to respond quickly to any abnormal IT activity. If a nurse, doctor or other staff member observes a failing system or suspicious message of some sort, they are to contact hospital security staff immediately. A “code dark” is then called, alerting employees to disconnect every digital device within reach. Doing so creates another perimeter of defense and can quarantine malware before is spreads systemwide.
Likewise, The Joint Commission notes that employees at all levels must be trained in how to respond to an attack after one happens. Full-scale exercises can simulate downtime events so staff members know how to access paper-based resources and redundant systems. It’s also wise to train staff in “clinical continuity plans” for the worst case. For example, how to treat a heart attack patient if imaging technology and cath labs are unavailable.
#4: Communicating through every available means
When the cyberattack happens, clear and decisive communications are needed in the moment. The attack might very well impact email, intranets and digital telephone systems. Alternate modes of communication including signs, flipcharts, portable radios and public address (PA) systems may be necessary to get the word out.
Regardless of the method, it’s vital that the following types of information be communicated as soon as it becomes available:
- Which systems are impacted, and which are not.
- Which clinical and non-clinical downtime procedures are in place.
- What is being done to address the situation, along with regular updates.
And the need to communicate doesn’t end with staff members. Patients, visitors and family members must be kept informed every step of the way as well.
#5: Backing up critical data and systems
Of course, even the best-trained employee can be fooled by a phishing scam and even immediate responses supported by detailed communications cannot undue malware damage already done. Another layer of defense is needed – one that ensures that up-to-date versions of clinical forms are continuously available no matter what.
A cybersecurity advisory titled Ransomware Activity Targeting the Healthcare and Public Health Sector was jointly published by CISA, the FBI and the Department of Health and Human Services (HHS). As noted in an earlier blog post, backup strategies were cited as a key defense against hospital ransomware attacks.
Specifically, healthcare organizations were encouraged to adopt a 3-2-1 approach to backups. That is, save three or more copies of all critical data in at least two different formats with one copy stored entirely offline, inaccessible to cybercriminals.
Such backup strategies are the most powerful defense currently available to healthcare organizations. However, backups are best viewed as complementary to the other two approaches noted above. It may be helpful to think of them as concentric circles rather than independent options:
- Level 1–Engage health information technology (HIT) professionals to develop a 3-2-1 backup strategy such as that outlined by CISA, the FBI and HHS.
- Level 2–Train all hospital staff members to recognize phishing and social engineering scams on sight and to alert hospital security immediately so a “code dark” protocol, such as that created by Children’s National Hospital, can be implemented.
- Level 3–Ensure that hospital staff members have instant, uninterruptible access to key clinical forms in the event of a downtime event–regardless of cause. Doing so is an example of a 3-2-1 backup strategy in action.
iMedDowntime: A Proprietary Strategy for Unplanned Downtime
iMedDowntime, available only from Taylor Healthcare, is a complementary backup strategy for unplanned downtime periods like those resulting from a ransomware attack. With iMedDowntime, a hospital or clinic can maintain normal operations without sacrificing efficiency or the quality of patient care –regardless of the status of its network or the type of malware used.
- Registrars can search patient records and print admissions packets while the admission, discharge and transfer (ADT) system is down.
- Nurses can print forms, labels and wristbands complete with patient demographics and barcodes.
- Physicians can access condition-specific protocols and continue to provide the same level of care as if the network was still live.
Best of all, iMedDowntime makes the stockpiling approach –and all of the drawbacks that come with it –entirely unnecessary. iMedDowntime is software designed to quietly reside within individual computer workstations and “wait” in the background until needed. If a downtime event occurs, hospital staff simply access the most up-to-date versions of the clinical forms and documents they need to sustain operations.
See how iMedDowntime is mitigating the risk of unplanned downtime events for healthcare systems nationwide. Contact your Taylor Healthcare representative to learn more.











